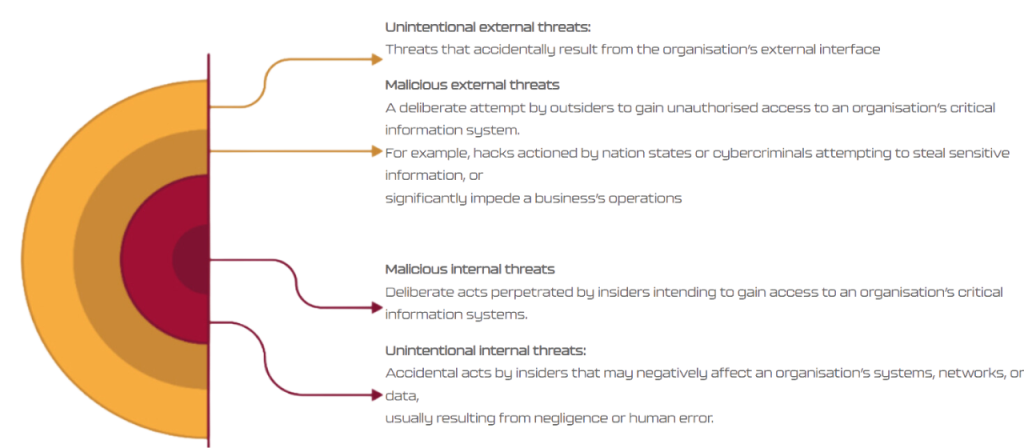
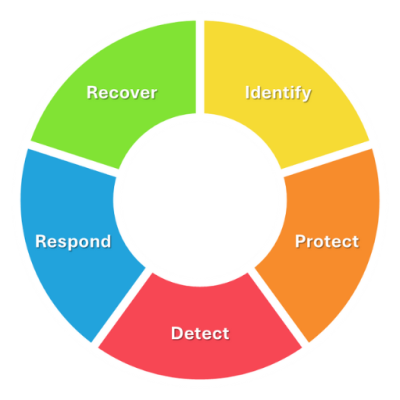
Create a secure and resilient cybersafe environment to protect our Cyber Safe Business members.
We provide support to protect privacy and ensure cyber safety, enabling an environment for achieving business innovation, growth and transparency.
Building Cyber Safety
Creating secure and resilient digital environments