Is Your State a Cybercrime Hotspot? Here’s Why Cybersecurity Should Be a Top Priority for Your Organ
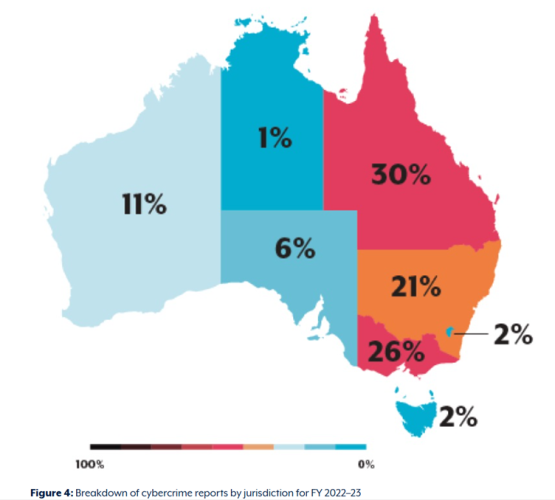
Are you aware that your location might be a major factor in the risk your organization faces from cybercrime? Across Australia, cybercrime is on the rise, with certain states and territories reporting significantly higher rates of incidents and financial losses. If your organization operates in Queensland, Victoria, New South Wales, or the Australian Capital Territory, […]
Cybercrime: A Growing Threat to Every Australian
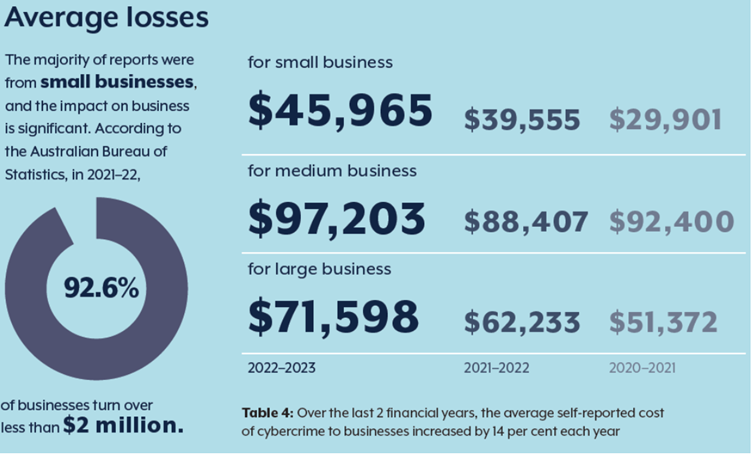
Reference Report from ASD Cyber Threat Report 2022-2023 Did you know that cybercrime has become a multibillion-dollar industry, threatening the safety and security of millions of Australians? Whether you’re an individual, a small business owner, or part of a larger organization, the risk is real—and growing. In 2022–23, cybercrime impacted millions across the country, inflicting […]
SaaS Deployments: Why Security Must Be a Priority for CISOs
Is your organization truly secure when it comes to Software-as-a-Service (SaaS) deployments? Many Chief Information Security Officers (CISOs) face a troubling reality: they hold accountability for security breaches without having direct control over SaaS implementations. This disconnect between responsibility and control can lead to serious security vulnerabilities. SaaS platforms are popular because they are easy […]
Ransomware Payments and Cryptocurrency Theft Surge in 2024
Are you keeping up with the latest trends in cybercrime? The first half of 2024 has seen alarming increases in ransomware payments and cryptocurrency theft, according to blockchain analysis firm Chainalysis. While some types of illegal on-chain activity have dropped, these specific cyber threats are on the rise. Chainalysis reports that ransomware payments have climbed […]
Is Your State a Cybercrime Hotspot?
A critical zero-click remote code execution (RCE) vulnerability, identified as CVE-2024-30103, was recently discovered in Microsoft Outlook. This flaw allows malicious actors to execute arbitrary code on a victim’s system simply by opening a specially crafted email. Review the details of this Cybersecurity Threat Advisory to limit your potential impact. What is the threat? CVE-2024-30103 […]
Millions of WordPress Sites at Risk Due to Critical Plugin Vulnerability
Are you running a WordPress site with the Litespeed Cache plugin? You could be vulnerable to a serious security risk. Millions of websites may be at risk of takeover due to a critical vulnerability found in this popular plugin. Litespeed Cache is a widely-used plugin designed to improve website performance by caching content. With over […]
Critical SAP vulnerabilities
SAP issued its August 2024 security patch update which included two critical flaws that enable attackers to bypass authentication and fully compromise affected systems. Review the details in this Cybersecurity Threat Advisory to learn how you can protect your SAP environment. What is the threat? SAP’s August security update addressed 17 vulnerabilities. Of the 17 […]
Stay compliant with the Barristers Rules – A complimentary webinar
Dear All, Are you confident in your compliance with the Barristers Rules, especially with growing cybersecurity threats on the horizon? We invite you to an exclusive CPD webinar presented by Cyber Safe Business, where Barrister Richard Douglas KC from Callinan Chambers and Hemmant’s List, and Alex Halim, CISO at Cyber Safe Business, will delve into […]
Thank You to All Who Joined Our August 2024 Webinar!
A huge thank you to everyone who attended and actively participated in our recent webinar, “Cyber Safe Business Practices for Barristers,” held in August 2024. It was a great success thanks to your engagement and enthusiasm! For those who couldn’t make it, don’t worry—we’ve got more valuable insights coming your way. Mark your calendars for […]
Google Warns of Active Exploitation of Chrome Vulnerability
Did you know your browser could be a gateway for cyberattacks? Google recently issued a warning about a significant vulnerability in Chrome that’s being actively exploited in the wild. This comes just days after the release of Chrome version 128, which addressed a previous zero-day vulnerability. The newly identified issue, tracked as CVE-2024-7965, has a […]